AWS Identity and Access Management:
Amazon Web Services (AWS) Identity and Access Management (IAM) is a service that helps securely control access to AWS resources. You can manage the resources that can be accessed, and what action can be performed. It allows you to manage access to AWS Services & Resources, such as
other Application Services & Resources in the AWS cloud
You can grant other people permission to administer and use resources in your AWS account without having to share your password or access key.
You can grant different permissions to different people for different resources.
You can use IAM features to securely provide credentials for applications that run on EC2 instances which provide permissions for your applications to access other AWS resources.
You can add two-factor authentication to your account and to individual users for extra security.
You can allow users to use identity federation to get temporary access to your AWS account.
You receive AWS CloudTrail log records that include information about IAM identities who made requests for resources in your account.
You use an access key (an access key ID and secret access key) to make programmatic requests to AWS. An Access Key ID and Secret Access Key can only be uniquely generated once and must be regenerated if lost.
IAM Important Elements:
1.Principal
An entity that can make a request for an action or operation on an AWS resource. Users, roles, federated users, and applications are all AWS principals.
Your AWS account root user is your first principal.
2.Request
When a principal tries to use the AWS Management Console, the AWS API, or the AWS CLI, that principal sends a request to AWS.
3.Authentication
To authenticate from the console as a user, you must sign in with your user name and password.
To authenticate from the API or AWS CLI, you must provide your access key and secret key.
4.Authorization
AWS uses values from the request context to check for policies that apply to the request. It then uses the policies to determine whether to allow or deny the request.
AWS Identity Access Management (IAM) works based on these parameters,
Identification: analyzing what kind of resource or source.
Authentication: who can access AWS resource.
Authorization: which resources users can access and what they can do to or with those resources.
Ways To Integrate With IAM:
AWS Identity Access Management (IAM) can be accessed via different methods, such as
Programmatic Access:
AWS Command Line Interface (AWS CLI)
AWS software development kits (SDKs)
IAM Implementation:
1. IAM User:
Instead of sharing your root user credentials with others, you can create individual IAM users within your account that correspond to users in your organization. IAM users are not separate accounts; they are users within your account.
Each user can have its own password for access to the AWS Management Console. You can also create an individual access key for each user so that the user can make programmatic requests to work with resources in your account.
By default, a brand new IAM user has NO permissions to do anything.
Users are global entities.
2.IAM Groups:
An IAM group is a collection of IAM users.
You can organize IAM users into IAM groups and attach access control policies to a group.
A user can belong to multiple groups.
Groups cannot belong to other groups.
Groups do not have security credentials and cannot access web services directly.
3.IAM Role:
A role does not have any credentials associated with it.
An IAM user can assume a role to temporarily take on different permissions for a specific task. A role can be assigned to a federated user who signs in by using an external identity provider instead of IAM.
AWS service role is a role that a service assumes to perform actions in your account on your behalf. This service role must include all the permissions required for the service to access the AWS resources that it needs.
AWS service role for an EC2 instance is a special type of service role that a service assumes to launch an EC2 instance that runs your application. This role is assigned to the EC2 instance when it is launched.
AWS service-linked role is a unique type of service role that is linked directly to an AWS service. Service-linked roles are predefined by the service and include all the permissions that the service requires to call other AWS services on your behalf.
An instance profile is a container for an IAM role that you can use to pass role information to an EC2 instance when the instance starts.
Users or groups can have multiple policies attached to them that grant different permission.
When to go for IAM User & IAM Role:
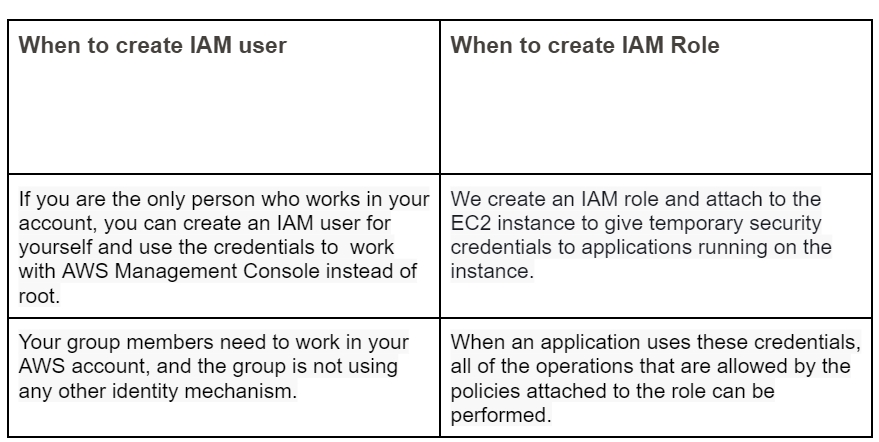
4.IAM Policy:
Most permission policies are JSON policy documents.
The IAM console includes policy summary tables that describe the access level, resources, and conditions that are allowed or denied for each service in a policy.
The policy summary table includes a list of services. Choose a service there to see the service summary.
This summary table includes a list of the actions and associated permissions for the chosen service. You can choose an action from that table to view the action summary.
To assign permissions to federated users, you can create an entity referred to as a role and define permissions for the role.
Types of IAM Policies:
AWS Organizations service control policies (SCPs):
Access control lists (ACLs):
Elements of IAM Policies:
Version: Specifies the current version of the policy language.
Statement: Contain an array of elements.
Effect: Whether the statement will result in an allow or an explicit deny.
Actions: Describes the specific action or actions that will be allowed or denied.
Resource: Specifies the object or objects that the statement covers.
Principal: Principal element specifies the identity.
Example:
Multi-Factor Authentication (MFA): IAM supports the use of MFA devices to provide an additional layer of security. MFA requires users to provide an additional authentication factor, such as a physical token or a virtual device, along with their regular IAM credentials.
Steps To Create IAM User:
1. login into management console:
2. Search IAM on service panel:
Note: IAM is a global service.
3. Then select users on IAM dashboard:
4. Then click create user:
5. Then name the IAM User:
6. Then selecting the access via management console option: under that select option: I want to create an IAM User.
7. Then under console password, there will two options select according to your preferences:
Then after that there will be option: Users must create a new password at next sign-in - Recommended, if you want you can select or else dis-select this option: click next.
8. Then under set permissions, there will be three options:
Add user to group. (if you want to add this user to an existing group click this option)
Copy Permissions. (if you want to existing permissions from a already created IAM User, click this option)
Attach policies directly. (if you want to policy directly to this IAM user, click this option)
9. I had selected third option on above, attaching the policy as per my preferences. You can add the policy according to your preferences or requirement. click next.
11. We can able to see the IAM user is created, click view user:
12. We could be able to see the Created IAM User details: